Data Breach Incident Report Template
Data Breach Incident Report Template - This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. Not all data breaches are caused by malicious third parties like hackers. You can use this data breach incident log template.
You can use this data breach incident log template. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. Not all data breaches are caused by malicious third parties like hackers. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner.
This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. You can use this data breach incident log template. Not all data breaches are caused by malicious third parties like hackers.
Free Cybersecurity (IT) Incident Report Template PDF Word eForms
Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. You can use this data breach incident log template. Not all data breaches are caused by malicious third parties like hackers. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective.
Data Breach Incident Report Template
Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Not all data breaches are caused by malicious third parties like hackers. You can use this data breach incident log.
Data Breach Incident Report Template
This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. You can use this data breach incident log template. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. Not all data breaches are caused by malicious third parties like.
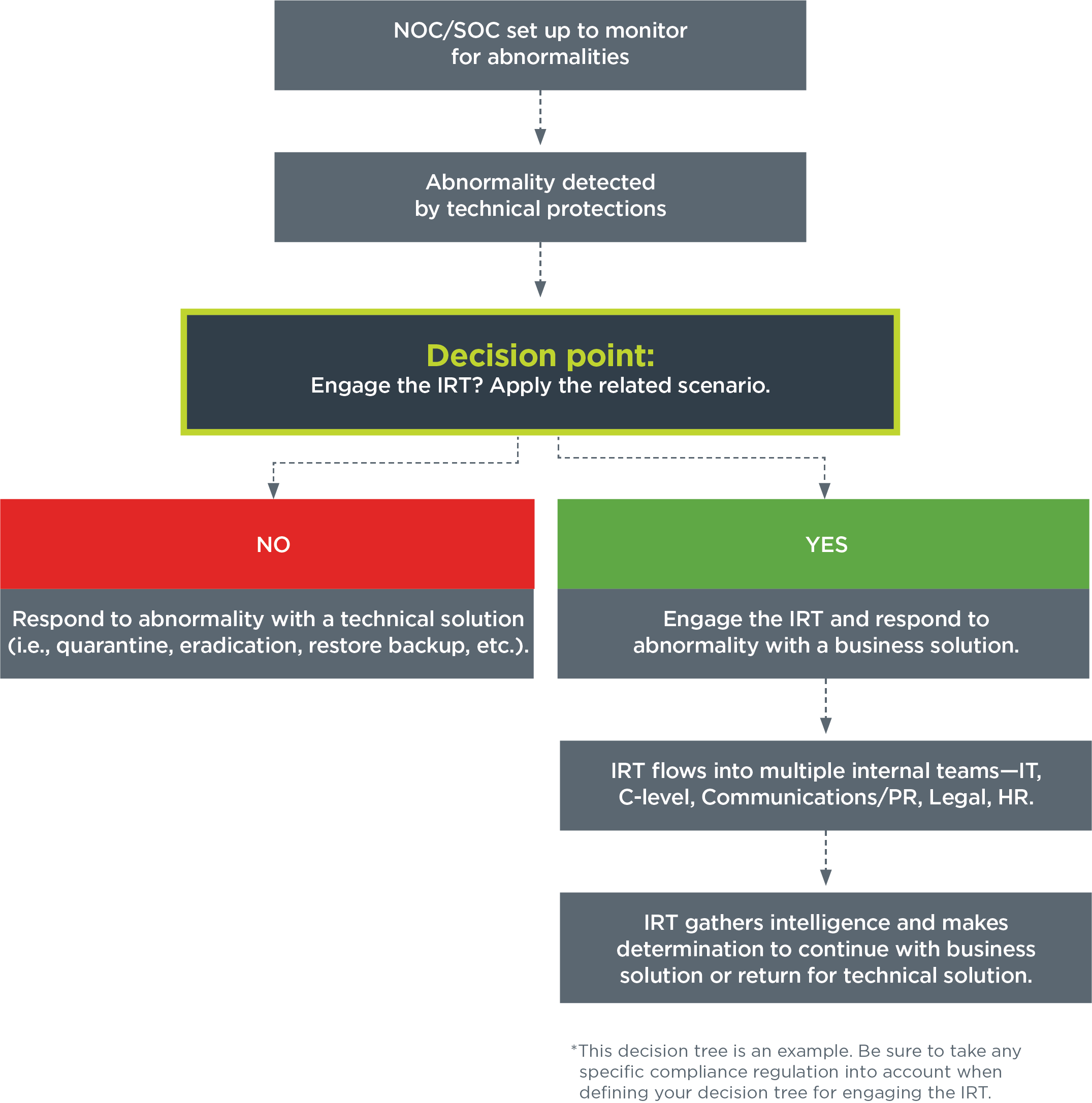
Cyber Security Incident Report Template Templates At In Software
Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. You can use this data breach incident log template. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Not all data breaches are caused by malicious third parties like.
Data Breach Plan Template
Not all data breaches are caused by malicious third parties like hackers. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. You can use this data breach incident log.
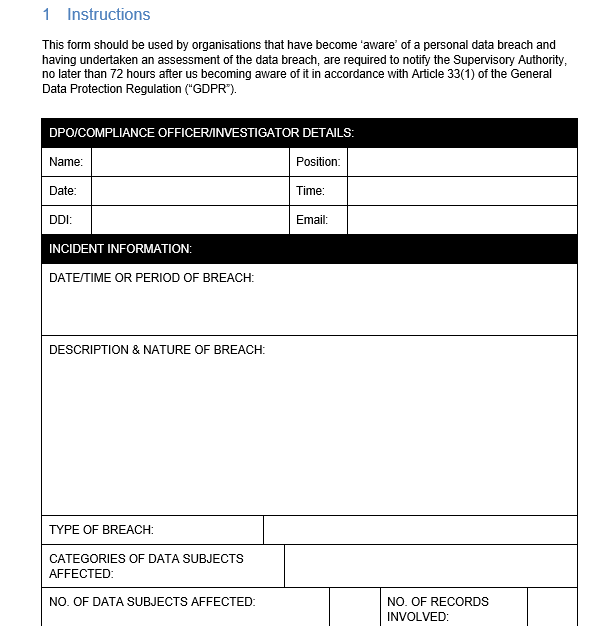
Incident Form for Data Breach (GDPR) GRCReady
This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. You can use this data breach incident log template. Not all data breaches are caused by malicious third parties like.
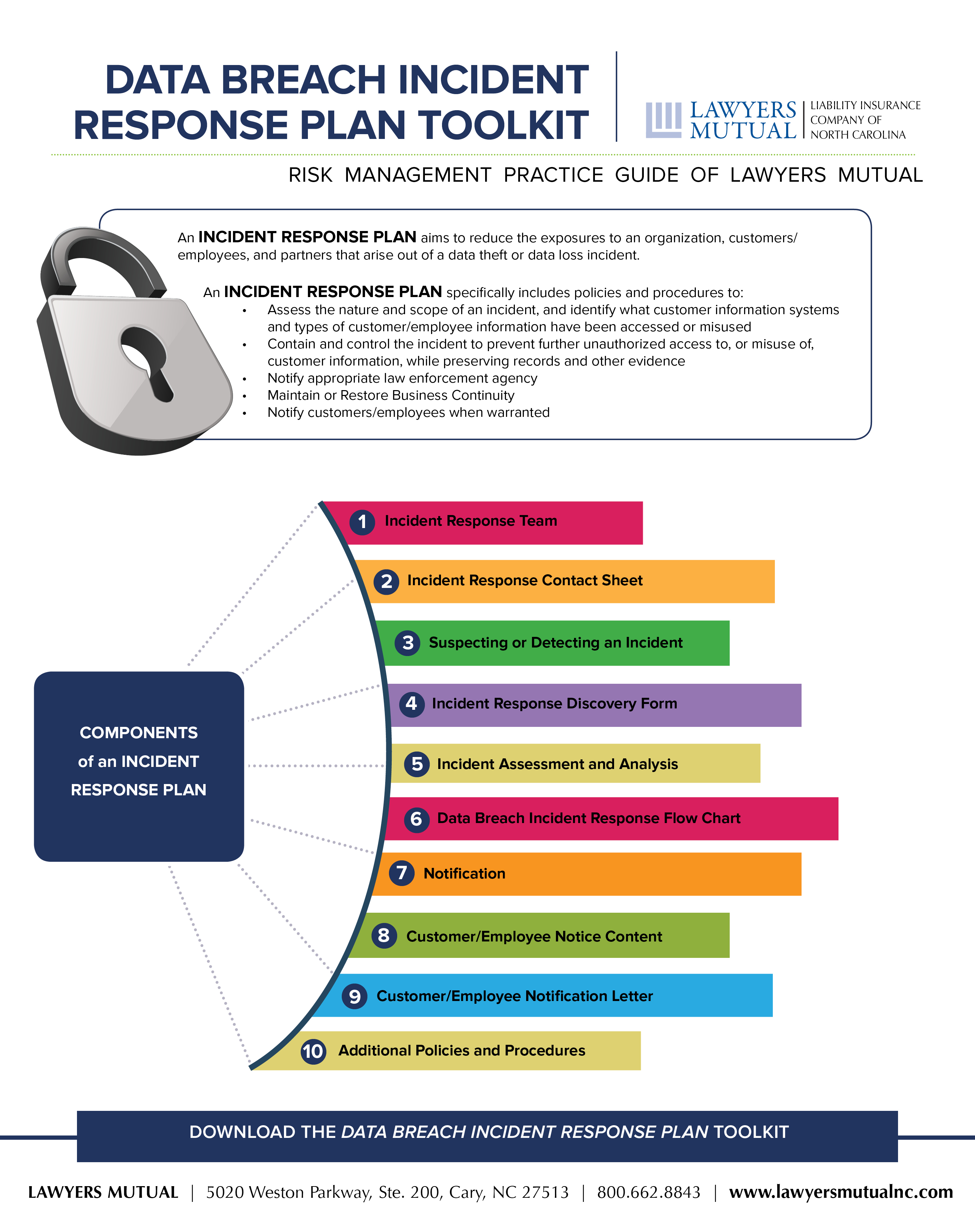
Data Breach Incident Response Plan Toolkit Infographic Lawyers
Not all data breaches are caused by malicious third parties like hackers. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. You can use this data breach incident log template. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential.
Security Breach Incident Report Template Printable Word Searches
Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. You can use this data breach incident log template. Not all data breaches are caused by malicious third parties like.
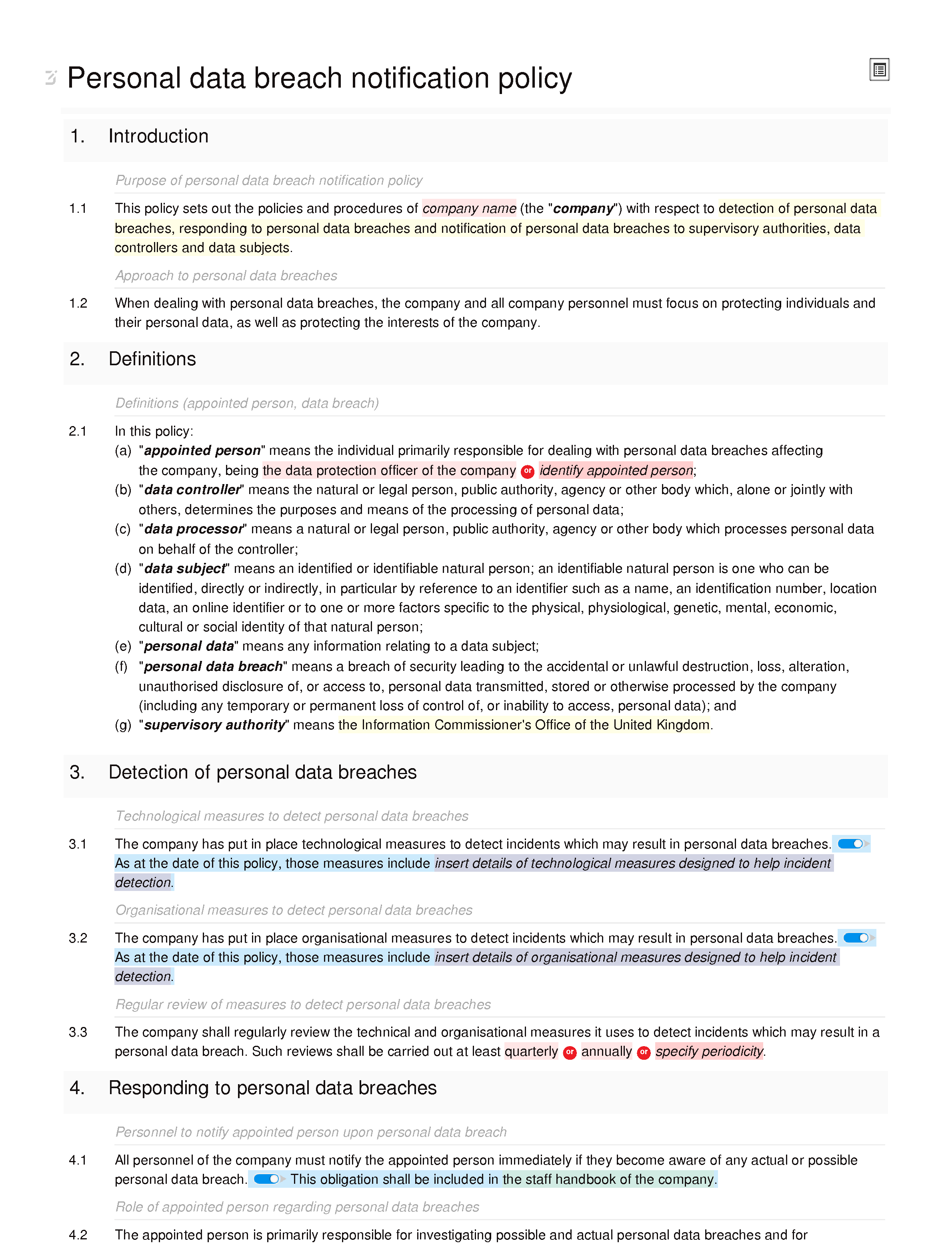
Data Breach Incident Response Plan Template
This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. You can use this data breach incident log template. Not all data breaches are caused by malicious third parties like.
Data Breach Reporting Template
Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes. You can use this data breach incident log template. This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Not all data breaches are caused by malicious third parties like.
You Can Use This Data Breach Incident Log Template.
This publication provides practical guidelines on responding to cyber security and data breach incidents in a consistent and effective manner. Not all data breaches are caused by malicious third parties like hackers. Provide a clear account of what happened, including systems or data affected, how the breach was discovered, and potential causes.